Introduction
CyberSecurity is a branch of Science that deals with threats faced by our Networks and works towards resolving those threats to keep our data safe and secure. Our entire World has moved over the network from money to work to communication. Everything can happen over the network but it becomes necessary to assure that no one’s identity is being faked and that data is available for use whenever needed. An Information System is an integrated structure which compiles software, hardware and human resource components to retrieve information and required in a manner that is useful.
Information Security
Information security refers to the safeguarding and protecting of information from unauthorised access, use and modifications.
This is done because information is that integral part of any organisation on which the organisations work. Thus, information is too sensitive and needs to be protected in order to keep it private, confidential and intact.
Information security is assured through a CIA model, Authentication, Authorisation, Non- repudiation
CIA stands for Confidentiality, Integrity and Availability.
Read about Data Security for information Security: What Is Data Governance | Importance Implementation and 5 Principles
Confidentiality
It assures that no information is accessed in an unauthorised manner. When information is transmitted over a network it happens in encrypted form so no one gets access to that information. For example a credit card number when travels over a network it does so in an encrypted format.
Integrity
Integrity means accuracy of information. The main of integrity is to keep the information intat as it is and protect it from unauthorized modification.
Availability
It means that data should be available to the user whenever required. What happens is that the hackers delete the data over the network and then it isn’t available when required.
Availability assures
- It assures Concurrency Control over a network.
- It provides data on time.
- It assures allocation of resources over a network.
Authentication
The sender and the receiver of the information over a network should confirm each other’s identity. The verification of identities are done through a username and password. This process of verification of identities is known as Authentication.
Authorization
Authorization is done through Access Control. It can be defined as a privilege given to a process which allows that process to access a computer resource over a network.
Non Repudiation
Non Repudiation ensures that the sender or the receiver cannot deny at the later stage that the information was transmitted or received by them. An example of the same is Digital Signature.
Pillars of Data Governance for Cyber Security, You should know: 4 Pillars Of Data Governance Framework: Guide To Successful Data Governance
Threats to Information System
Anything that can harm the security of the system and the information stored in it by using the vulnerability of a system is termed as threat.
Threats can be:
- Intentional
- Unintentional
- Natural
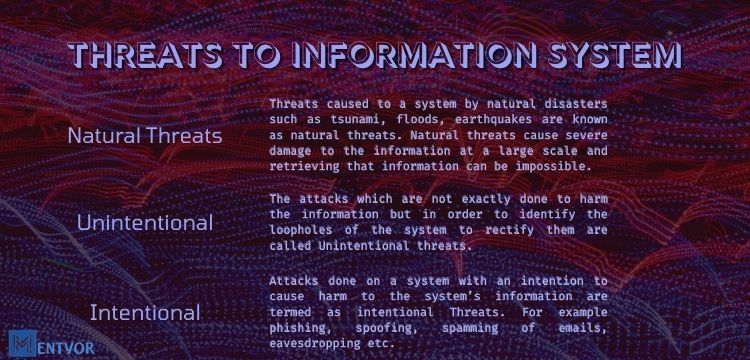
Natural Threats
Threats caused to a system by natural disasters such as tsunami, floods, earthquakes are known as natural threats. Natural threats cause severe damage to the information at a large scale and retrieving that information can be impossible.
Unintentional
The attacks which are not exactly done to harm the information but in order to identify the loopholes of the system to rectify them are called Unintentional threats.
Intentional
Attacks done on a system with an intention to cause harm to the system’s information are termed as intentional Threats. For example phishing, spoofing, spamming of emails, eavesdropping etc.
Security Technology
With all the threats lingering over the network it becomes necessary to identify the loopholes of the security system and rectify them so that our information can remain preserved. This can be done by strengthening the security system through various Security technologies.
These technologies include- cryptography, firewall, IDS ( IIntrusion Detection System), Digital Signature, VPN (Virtual Private Network) etc.
Developing a secure System
It is essential to develop a secure system in order to protect our information from threats.
Objectives:
- To ensure that CIA model is followed
- To ensure that all the security flaws are reported.
- To ensure that the information is not revealed to someone who isn’t a part of the organization or that communication.
- To ensure the prevention of unauthorized access and provide strength to internal controls.
Management Commitments:
It helps in handling security issues and leads to decrease in likelihood of failure.
It ensures support to business units.
Every individual should follow the security guidelines and practises given by the authenticated sources
Responsibilities:
The security team is responsible for developing security programs in order to keep the information secure.
People from management are responsible for designing security policies and guidelines.
The team responsible for designing security information systems should be well aware of recent business culture and technologies in use.
Read more about Cloud Computing for Cyber Security: What is Cloud Computing Technology ?
Importance of CyberSecurity

- It protects information from damage.
- It protects the system from any malicious attack.
- It protects any unauthorised access to our information and system.
- It helps in communication of data breaches.
- It helps in storage of sensitive data
- It protects data through techniques like cryptography and digital signature.
- It protects data and systems from viruses, worms and trojan horses.
- It helps in detection of any malicious activity over a network.
- It helps in making data available as and when required.
- It ensures that data available is not modified over the network.
Cyber crime

With the increase in communication, cyber crime has grown tremendously. Cyber crime is a term used when any individual is threatened about something over the network. Cyber bullying and cyber terrorism are examples of such cyber crime and thus in order to avoid these crime over the network cyberlaw has gained popularity too.
Cyber laws ensure severe punishments to people indulging in cyber bullying.
Examples of these cyber crimes are:
- Acid threats on social media
- Morphing of images and using them to threaten people
- Abusing people over the network with a hidden identity
- Faking identity for malicious activities
Cyber law has come into play and is now a very popular branch of Law.
Conclusion
Cybersecurity has become the need of the hour. With all sensitive data and information stored over a network it becomes extremely necessary to protect that data from unauthorised access as well as its security so that identities do not get faked. With increasing automation around the world, protection of each and everything used and preserved over a network becomes extremely important and thus it is the most widely growing area of computer science. Organisations are spending billions and millions to keep their data protected and safe from threats or hackers.
Cyber security has the most readily growing market in recent times and it is speculated to grow over years as we move towards a completely digitalized world.
Cyber security uses cryptography in order to encrypt data over a network and decryption of the same happens over the other end.
Cyber threats and their prevention is a vast topic to study about and thus automatically makes cyber security an important technology.
Cyber crime has a vast impact on an organisation where the organisation suffers economic losses, reputational losses and also loses the trust of its clients and employees.
FAQs (Frequently Asked Questions)
- What are the different types of cyber security?
There are 5 different types of cyber security namely Internet of Things (IoT), Application Security, Network Security, Cloud security and Critical Infrastructure Security. - Is Computer programming necessary for Cyber Security?
No, If you are at an entry-level you wouldn’t require computer programming but as you proceed to mid and higher levels you will need the knowledge of computer programming. - Which Language is used for hacking by the hackers?
Python is used by hackers for hacking purposes. - What is the main aim of Cyber Security?
The main aim of cyber security is to prevent privacy breach, Ensure the data transferred and used is correct and ensure there is no unauthorised access to someone else’s data. - Who is the number 1 hacker around the world?
Kevin Mitnick is the most famous hacker in the world. - What is the future of cyber security?
Cyber security is the most rapidly growing technology in the market and has very high market investment. Governments and organisations spend a lot to prevent the confidentiality of their data and protect data breach. - Who hacked the Website of NASA?
Gary McKinnon, a Britisher, hacked the Website of NASA.
References
- Cybersecurity: What Everyone Needs to Know By Peter W. Singer, Allan Friedman
- “Cybersecurity.” IEEE Xplore, ieeexplore.
- “Investigating the Impact of Cybersecurity Policy Awareness on Employees’ Cybersecurity Behavior.”
- “Cybersecurity Data Science: an Overview from Machine Learning Perspective.” SpringerLink, 1 July 2020,


 WhatsApp
WhatsApp