Introduction
Cryptography is the art of writing messages in a secret format so that it can only be understood by the person for whom the message is meant. It is nothing new and this art is dated to be first used in the 1900s. Though a lot of people believe cryptography emerged on its own when writing was invented, it can’t be believed.
It was orally practiced in the ancient times when people used to code the messages and tell their messenger to tell this to someone and that person will understand. However, it has developed and taken new forms since the technology has grown. Computer Science and its growth has given a great shape to cryptography so that data can be secured and wisely sent.
Any system needs a few security checks to be done which include Authentication, privacy, non-repudiation and integrity.
Thus Cryptography has a large scope; it is used for user authentication alongside being used for encryption and decryption of data.
Read about Cloud Computing: What is Cloud Computing Technology ?
Types of Cryptographic Algorithms
Cryptographic algorithms are classified into three. This classification is done on the basis of the number of keys involved and their use. These algorithms are:
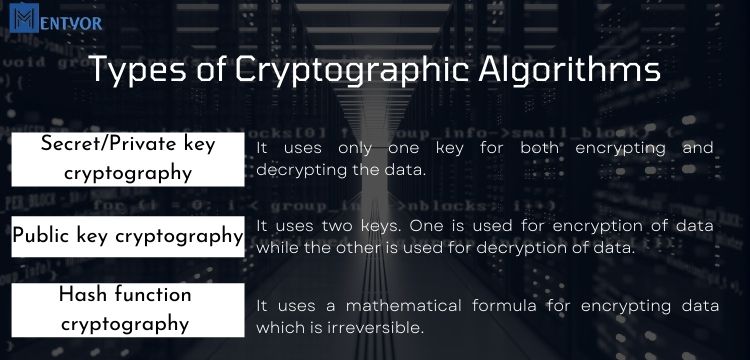
Secret/Private key cryptography
It uses only one key for both encrypting and decrypting the data.
Public key cryptography:
It uses two keys. One is used for encryption of data while the other is used for decryption of data.
Hash function cryptography:
It uses a mathematical formula for encrypting data which is irreversible.
Secret Key Cryptography
As we know that in secret key cryptography only one key is used to encrypt and decrypt the data.
If I am encrypting the data I know both the information and the key. After encryption data is transmitted to the receiver. Now since only one key is used it is necessary that the receiver also has the key so that he can decrypt the data. This comes as the biggest challenge in secret key cryptography. The key needs to be transmitted as well.
This method thus includes ciphers. They are either block ciphers or stream ciphers.
Stream ciphers keep changing constantly and they work on a single bit. Whereas block ciphers encrypt one entire block of data at the given time.
Public Key Cryptography
Public key cryptography is comparatively similar. It can be done over a network which isn’t secure. Two keys are involved in the communication out of one is used in encryption and the other in decryption. There is no need for key transmission as both the sender and the receiver have a key.
Out of two keys one is public that is known to all and another is a secret that is only to the parties involved in the communication. The combination of public and private key is used to receive data and decrypt it.
Hash Function
Hash functions are used for encryption which happens one way. It is a mathematical algorithm used to transmit encrypted data which is irreversible. There is no key involved. What happens is a hash code of a certain length gets added to the text which makes it impossible for the text to be modified. It is mostly used for encryption of passwords.
Read about Blockchain Technology: Blockchain – The Most Talked Technology of today’s Era
Why are so many techniques needed for encryption?
The three different techniques are used for encryption because every method has its own significance. Hash functions are mainly used to maintain the integrity of the data. Since it is an algorithm that depends on text length as soon as the data gets altered so does the hash code. It thus signifies that the data has been altered.
Secret key on the other hand is used for end to end encryption. Though key transmission does become a task but working in a not so secure network, secret key encryption becomes more advantageous.
Public key encryption is done when the data needs to travel but not the key. Thus the transmission of key challenges are eradicated.
There is a hybrid scheme of cryptography which merges all these techniques and forms a digital envelope. This is a digital signature.
Digital Signature

A digital signature is made up of a digital envelope and a session key.
- The sender first encrypts his message using a session key through the secret key cryptographic scheme.
- Then the sender encrypts the session key using the receiver’s public key.
- The digital envelope is thus formed consisting of an encrypted message and the encrypted key.
- The data is then transmitted over the network.
- On receiving the digital envelope, the receiver decrypts the message using his private key.
Digital signature thus a two step verification. First the sender computes the hash value of his message. He then encrypts that hash value with his own private key the data then gets transferred. The receiver then decrypts the hash value first by using the sender’s public key and then applies the hash value to the original message sent by the sender. If the retrieved hash values are the same the data has travelled unaltered but if the hash values are not same the data has been altered in the path and the information has been hacked.
Digital Signature works to provide security of data and non-repudiation. If the sender has generated the hash value he justifies that he is the sender and if the receiver has rightly decrypted the data he proves of him being the intended receiver. Thus digital signature works on all the schemes of cryptography combined.
Also Read about Data Governance for Data Security: What Is Data Governance | Importance Implementation and 5 Principles
Significance of cryptography

- It ensures secured transactions
- Protects data from being modified
- It ensures protected communications.
- It helps in maintaining data confidentiality
- It helps in establishment of trust between servers
- It helps in safeguarding personal information
- It helps in ensuring that data is being accessed by an authenticated user.
- It is highly secured and has very few chances of attack.
- It ensures non-repudiation
Drawbacks of Cryptography
Every coin has two sides and so does cryptography. It comes with its own set of disadvantages. Few of them are:
- It cannot safeguard the threats that arise due to poor designing of the systems
- Availability of data is not ensured when cryptography gets involved into the picture.
- It is both a costly and time-consuming process.
Read about Cryptocurrency usage in Metaverse: Investing in the Metaverse: Different Cryptocurrencies in Metaverse and Technology Behind
Conclusion
Cryptography has scope for growth. The world has moved towards Digitalisation and data is the most important part of anything that works on and around Computers. Information is what needs to be transferred, processed, gathered and displayed. In such scenarios it becomes extremely essential that the data is protected and doesn’t reach the wrong hands. Thus it becomes important in itself for it is the technique used to keep the most important aspect of computer communication secure and available.
FAQs (Frequently Asked Questions)
- Name the three types of Cryptography?
The three types of cryptography are:
Secret Key Cryptography
Public Key Cryptography
Hash Functions Cryptography - For what Cryptography is used?
It is used to secure data travelling over the network so that it is not modified and is kept intact. - What does master key refer to in cryptography?
Master Key refers to the key that is used to encrypt all the systems involved in a network in cryptography. - Does Blockchain involve any kind of cryptography?
Yes, blockchain uses cryptographic concepts. Data stored in each block is encrypted and then stored to hide the details of the participant who is involved in the transaction. - What is the difference between cryptography and encryption?
It is the technique to secure data. It involves the study of methods like encryption, digital signature etc.Whereas Encryption is the algorithm that is put to use in order to conceal messages. - What is the future of cryptography?
It is the most rapidly growing technology in the market and has very high market investment. Governments and organizations spend a lot to prevent the confidentiality of their data and protect data breach. Cryptography is the need of the hour and requires extensive understanding of programming concepts and expertise over the field. - What do you mean by crypto-analysis?
To check a system which is cryptographed in order to find loopholes and restore them is called crypto-analysis.It is done in order to minimise the risk of data modulation and its security breach.
References-
- “Nonmalleable Cryptography.” SIAM Review, 4 Aug. 2006, epubs.siam.org/doi/abs/10.1137/S0036144503429856.
- “An Overview of Cryptography” Computer Science Department at Princeton University,
- “New Directions in Cryptography | Whitfield Diffie, Martin E. Hellman |.” Taylor & Francis,
- “Introduction to Modern Cryptography.” Google Books
- “Cryptography.” ScienceDirect.com | Science, Health and Medical Journals, Full Text Articles and Books,


 WhatsApp
WhatsApp